https://cryptohack.org/courses/intro/xor1/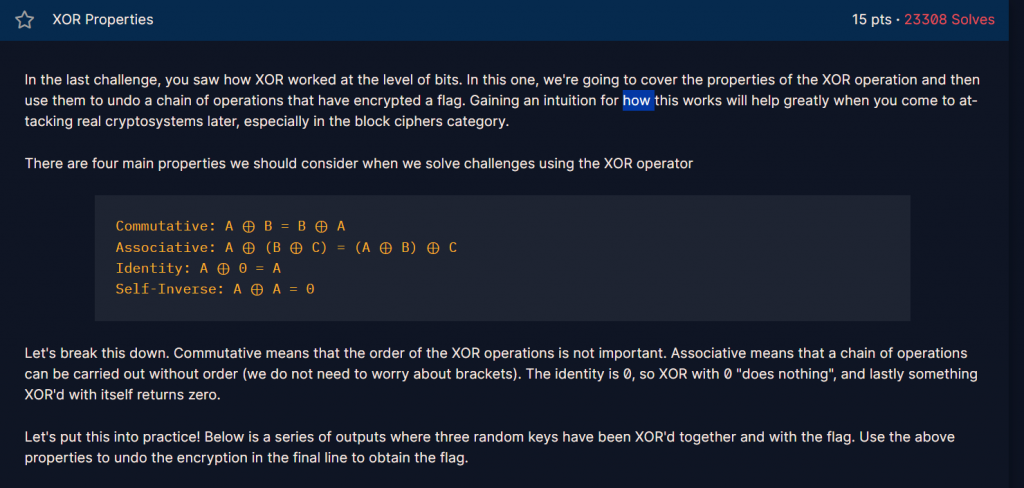
再來回顧一下xor的性質
A ⊕ B = B ⊕ A
A ⊕ (B ⊕ C) = (A ⊕ B) ⊕ C
A ⊕ 0 = A
A ⊕ A = 0
(A ⊕ B) ⊕ B = A
利用xor的性質,解出flag
KEY1 = a6c8b6733c9b22de7bc0253266a3867df55acde8635e19c73313
KEY2 ^ KEY1 = 37dcb292030faa90d07eec17e3b1c6d8daf94c35d4c9191a5e1e
KEY2 ^ KEY3 = c1545756687e7573db23aa1c3452a098b71a7fbf0fddddde5fc1
FLAG ^ KEY1 ^ KEY3 ^ KEY2 = 04ee9855208a2cd59091d04767ae47963170d1660df7f56f5faf
from pwn import xor
#要記得將題目給的物件轉成bytes格式
k1 = bytes.fromhex('a6c8b6733c9b22de7bc0253266a3867df55acde8635e19c73313')
a1=bytes.fromhex('37dcb292030faa90d07eec17e3b1c6d8daf94c35d4c9191a5e1e')
a2=bytes.fromhex('c1545756687e7573db23aa1c3452a098b71a7fbf0fddddde5fc1')
a3=bytes.fromhex('04ee9855208a2cd59091d04767ae47963170d1660df7f56f5faf')
# a1 = k2^k1 = 37dcb292030faa90d07eec17e3b1c6d8daf94c35d4c9191a5e1e
# a2 = k2^k3 = c1545756687e7573db23aa1c3452a098b71a7fbf0fddddde5fc1
# a3 = Flag^k1^k3^k2 = 04ee9855208a2cd59091d04767ae47963170d1660df7f56f5faf
# k4=k1^k2^k3
k2= xor(k1,a1) # k1^(a1)= k1^(k1^k2)=(k1^k1)^k2 = k2
k3=xor(k2,a2) # k2^(a2)=k2^(k2^k3)=(k2^k2)^k3 = k3
k4=xor(k3,a1) # k3^(a1)=k3^(k1^k2)=k4
Flag=xor(k4,a3) # k4^(a3)=(k3^k1^k2)^(Flag^k1^k3^k2)=Flag
print(Flag)
crypto{x0r_i5_ass0c1at1v3}
也就是(crypto{xor_is_associative},xor是可交換的)
https://cryptohack.org/courses/intro/xorkey0/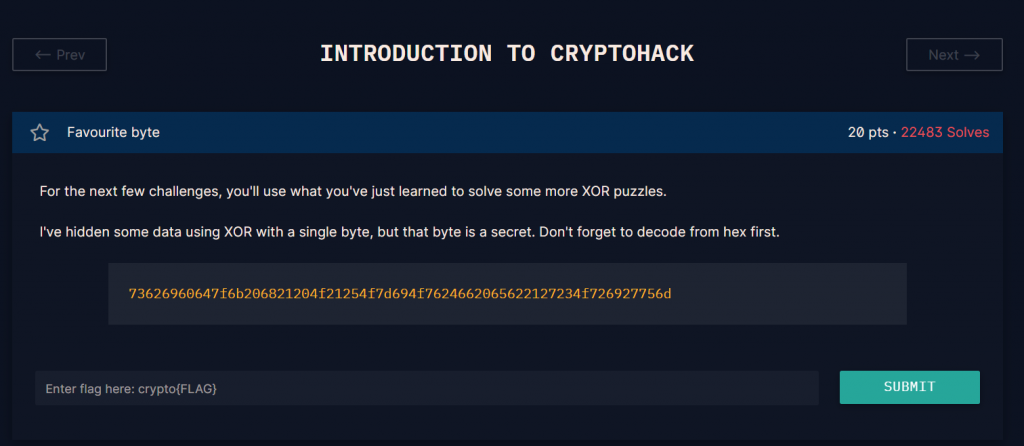
from pwn import xor
k1=bytes.fromhex('73626960647f6b206821204f21254f7d694f7624662065622127234f726927756d')
for i in range(256):
k2=xor(k1,i).decode() #decode:將bytes轉string
if(k2[0:6]=='crypto'): #因為flag的形式是crypto{},所以若解碼後的前六碼為crypto,則輸出。
print(k2)
break
crypto{0x10_15_my_f4v0ur173_by7e}
crypto{0x10_is_my_favourite_byte},以print(hex(i))檢查了一下,發現密鑰真的是0x10
今天解了兩題xor題目。剩下的明天繼續解~
